Needham-Schroeder protocol Explained

This post will be a major prerequisite for understanding our kerberos documentation. In this post we will be concentrating on Needham-Schroeder protocol which is used in kerberos for secure authentication. We will not be discussing kerberos in this post, but will be discussing the main prerequisite for understanding kerberos infrastructure. Because Kerberos infrastructure relies on Needham-Schroeder protocol.
Needham-Schroeder protocol reffers to a communication protocol used to secure an insecure network. The protocol got its name from the creaters Roger Needham and Michael Schroeder.
There are twotypes of Needham-Schroeder protocol.
- Needham-Schroeder protocol with symmetric key
- Needham-Schroeder protocol with assymetric key
Now lets understand Needham-Schroeder protocol with symmetric key encryption because its the one used in kerberos infrastructure.
Needham-Schroeder protocol allows to prove the identity of the end users communicating, and also prents a middle man from evesdropping.
We will be using some terms in this document which needs to be understood first.
Nonce: Nonce is a randomly genrated string which is only valid for some period of time, This is used in encryption protocols to prevent replay attack. For example if somebody captures a packet during the communication between me and a shopping website, he can resend the packet without decrypting it, and the server can accept the packet and do operations on it. To prevent this, nonce(the random value generated) is added to the data, so as the server can check if that nonce is valid, or expired.
Lets understand this protocol by taking an example communication between two machines called Machine A and Machine B.
The main thing in this protocol is that there is a trusted middle man or call him an arbitrator. This trusted middle man is a server. If an X machine wants to communicate, with Y machine, then X has to contact the middle man server, saying am interested in communicating with Y.
Lets see how this works.
A = Machine A
B = Machine B
SK(AS) = this is the symmetric key known to Machine A and middle man Server named “S”
SK(BS) = this is the symmetric key known to Machine B and middle man Server named “S”
NON(A) = Nonce generated by Machine A
NON(B) = Nonce generated by Machine B
SK(S) = this is the symmetric key/session key generated by the server for both machine A and Machine B.
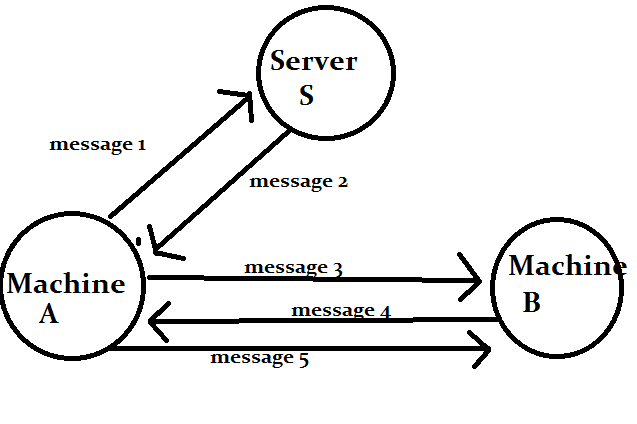
Lets understand all the messages above mentioned.
Initially before going ahead with the explanation, make it clear that the symmetric keys of both machine A, Machine B are already shared with the Middle Man server. Also any other machine in the network also shares its respective Symmetric keys with the Middle Man server.
Message 1: Machine 1 sends a message to Server S saying that i want to communicate with Machine B.
A -> S: (this message contains A and B and NON(A))
Message 2: Server S sends message 2 back to Machine A containing SK(S), and also one more copy of SK(S) encrypted with SK(BS), this copy will be send to Machine B by Machine A.
Message 3: Machine A forwards the copy of SK(S), to Machine B, who can decrypt it with the key it has because it was encrypted by the Middle man server with the Machine B's symmetric Key SK(BS).
Message 4: Machine B sends back Machine A a nonce value encrypted by SK(S). to confirm that he has the symmetric key or session key provided by the middle man server.
Message 5: Machine A performs a simple operation on the nonce provided by the Machine B and resends that back to machine B just to verify Machine A has the key
There are still some vulnerability in this protocol for replay attacks which is fixed by the timestamp implimentation in this, when used by kerberos.
Hope you all understood the protocol...any doubts/questions are welcome(through comments.)


 Sarath Pillai
Sarath Pillai Satish Tiwary
Satish Tiwary
Comments
Very nice!
Very nice!
Good description...Preety
Good description...Preety helpful....Thank you..!!!
explained well
explained well, thnk u
query
I understand what it is. But could you please tell me where it is used in real life?
It is used in various
It is used in various institutions, like, for example in Oracle, where I worked as an intern, we used kerberos login extensively, every single day. To authenticate the changes/commits in the code.
best explanation
<html>
<head>
Techstar*
</head>
<body>
That was one of the best explanation i ever find thank you
</body>
</html>
Very useful and good
Very useful and good
Add new comment